Other services
Armed with proficiency in multiple security application tools, network technologies and operating systems, as well as a knack for translating complex security aspects into business terms, we cover a wide range of industries from E-commerce, Medical, Telecommunication, custom software products and many others.
IoT Security
CTS's IoT Security solutions are driving innovation so that we can all realize the benefits of a totally connected world.
When securing IoT we take care of: the device, the
cloud infrastructure, the network.
We have experience testing every major type of web service, including SOAP, REST and custom protocols, and can work with any form of authentication, from OAUTH tokens to client certificates and custom digital signatures.
Web services security
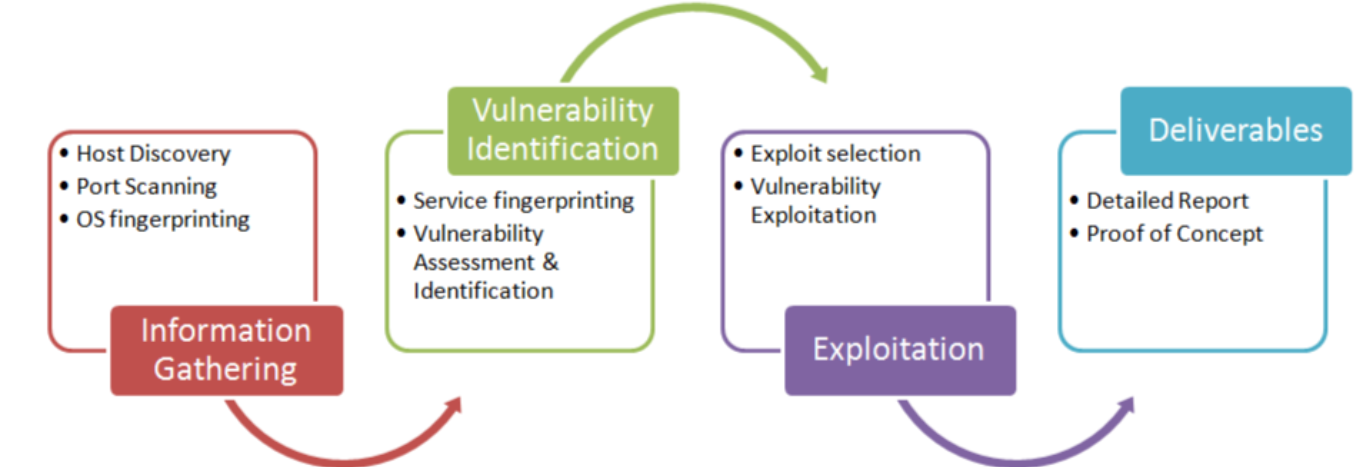
General Internal network approach
Anti-piracy actions
Investigations
In case your software products are pirated we can investigate and can take the right actions to stop piracy and software theft.
Training and consultancy
Experience the industry’s most realistic penetration testing security training courses. Taught by the ethical hackers that went through hundreds of pen-tests.
Capabilities
Unlock an information security strategy that aligns with an organization’s current and future objectives.
A rapid, cost-effective way to access the expertise and knowledge of experienced professionals who can oversee the security and protection of your business.
We provides expert training ranging from technical security education to general security awareness programs.
Our services
Auditing is a specific know-how which requires knowing not only the products involved but also the profession of the user of the audited means. It follows a precise audit book defined with the client. It may rely on third-party tools for vulnerability or performance testing.
Defining specifications is an exercise that requires knowing both the targeted products and above all the objective that we want to achieve.
The evolution of your architecture is a necessary step and very often planned in advance, if only in terms of depreciation, but which must take place without any impact on the user side. You may need to evolve your architecture in terms of product or in terms of function.
Defining comprehensive policies is always a delicate matter in terms of both design and application. CTS, drawing on its feedback from customer experiences, can help you define global policies, the implementation of which remains possible.
Thanks to its knowledge of your business, its project management skills and above all its technical mastery of the elements that make up the response to your needs, CTS can take charge of the management of a technical project at your place. The definition of constraints, impacts, respect for the schedule and the management of teams and resources will be the responsibility of CTS. This assures you of the simplified management of your project with a guarantee of CTS results on the good progress of the latter.
CTS carries out numerous solution studies for our customers to ensure that the chosen solution perfectly meets the needs. These tailor-made studies take into account the customer's environment as well as its various constraints and aim to highlight the most suitable solution in the customer context.
Resources
- Explosion in digital commerce pushed fraud incentive levels sky-high November 17, 2020
- Researcher Discloses Critical RCE Flaws In Cisco Security Manager October 14, 2020
- Ransomware: A Lucrative Business Model for Hackers, says FS-ISAC October 1, 2020

